iptables snippets
iptables is the default firewall you see on any linux computer. It works by allowing (ACCEPTing) or denying (DROPing) connections to the local computer. There are basically three scenarios you can deal with:
- INPUT: Connections generated from a different computer targeting yours; for example, when you run a web server on your computer and others want to connect to it.
- OUTPUT: Connections generated from your computer targeting other computers; for example, when you open a web page or open a remote ssh session.
- FORWARD: Connections generated from computers different than your, but that use your computer as a link to get to other computers; for example, when you share your computer’s internet connection with others, that is, when you use your computer as a router for others.
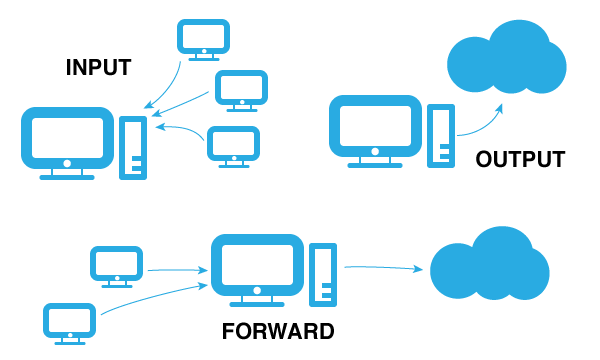
Here I have a small compilation of some useful tasks for iptables. I hope you find them useful.
Adding rules
1iptables -A INPUT -i lo -j ACCEPT
What it does: Instructs iptables to allow all incoming connection from localhost. This is a required rule, since many programs use TCP to make local connections.
1iptables -A INPUT -p tcp --dport 22 -j ACCEPT
What it does: Opens port 22 (SSH) to TCP connections coming from any computer.
1iptables -A INPUT -p tcp -s 192.168.1.2 --dport 3306 -j ACCEPT
What it does: Opens port 3306 (MySQL) to TCP connections coming from IP address 192.168.1.2.
1iptables -A INPUT -p udp --dport 53 -j ACCEPT
What it does: Opens port 53 (DNS) to UDP connections coming from any computer. Important: DNS requires both UDP and TCP to work properly.
1iptables -P INPUT DROP
What it does: Denies all incoming connections (generated from the outside world to your computer), no matter what port you are trying to connect to.
1iptables -P FORWARD DROP
What it does: Denies all forwarding connections. If you do this, your computer will not work if you want to share your computer’s internet connection to other computers. You usually want to deny it.
1iptables -P OUTPUT ACCEPT
What it does: Allows all connections generated from the local computer (localhost) to the outside world. If you do not allow them, you will not be able to surf the web!
Listing current rules
1iptables -L
What it does: Prints the list of current rules.
1iptables -vL
What it does: Prints the list of current rules, but includes more information (v = verbose).
1iptables -vnL --line-numbers
What it does: Prints the list of current rules including a column with line numbers; They are useful to make reference to a particular rule by number.
Deleting a rule
1iptables -D INPUT -s 192.168.1.1 -p tcp --dport 111 -j ACCEPT
What it does: Deletes the rule that allows TCP connections on port 111 from IP address 192.168.1.1.
1iptables -D INPUT 4
What it does: Deletes rule number 4. (Do you remember how to print the list of rules along with its line numbers? Well, this is an easy way to delete a rule.)
1iptables -F
What it does: Deletes all the rules (F = flush). Be careful when you run this!
Saving your current rules
1/sbin/service iptables save
What it does: Saves the current rules to disk, so they are applied next time you turn your computer on.
A full example
1iptables -F
2iptables -A INPUT -i lo -j ACCEPT
3iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
4iptables -A INPUT -p tcp --dport 22 -j ACCEPT
5iptables -A INPUT -p tcp --dport 80 -j ACCEPT
6iptables -P INPUT DROP
7iptables -P FORWARD DROP
8iptables -P OUTPUT ACCEPT
9/sbin/service iptables save
10iptables -vL
An important thing to keep in mind is that all rules are applied from top to bottom. If you have a DROP rule before an ACCEPT rule, then the rule with the DROP wins. It is important that you add your rules in the order that you want them to be evaluated.
Here’s what the previous snippet does:
- Deletes all the rules
- Adds a rule to accept all incoming data packages coming from localhost. This is a must!
- This one is tricky. It loads iptables state module (-m state) and instructs it to allow all data packages from established and related connections. What??? We’ll get back to this in a moment…
- Adds a rule to accept TCP connections on port 22 (SSH) from any computer.
- Adds a rule to accept TCP connections on port 80 (Web) from any computer.
- Drops any incoming data packages. Wait, what??? Yes, remember that rules are evaluated from top to bottom. If we receive a connection request on port 80 (line 5), it will be accepted, because that rule is before this one. The same will happen to local connections (because of line 2) and SSH connections (because of line 4). If we would place this drop rule on line 2, then we would be effectively blocking all incoming connections.
- Drops any forwarding package. We are not using our computer as a router, so this is the best.
- Allow all outgoing packages. So we can check Facebook!
- Save it. If you do not save it, all your work will be lost next time you restart your computer.
- Finally, take a look at it.
What about line 3? Well, it says, all data packages coming over a previously allowed connection, that is one from localhost or on ports 22 or 80, will be accepted without further checking. If your computer receives a new request for a web page (on port 80, of course) iptables will start checking all rules, one by one, starting by the first one. The one that will allow the connection is the rule on line 5. So data packages coming from that computer, using that same connection, will be allowed because there is an active and previously established connection. This is useful because this way iptables does not have to check all the rules again.
Some more iptables snippets
1iptables -A INPUT -p tcp --dport 22 -j ACCEPT
What it does: Allows SSH connections to local computer
1iptables -A INPUT -p tcp --dport 80 -j ACCEPT
What it does: Allows web connections to local computer
1iptables -A INPUT -p udp --dport 53 -j ACCEPT
2iptables -A INPUT -p tcp --dport 53 -j ACCEPT
What it does: Allows DNS connections to local computer
1iptables -A INPUT -p udp --dport 137 -j ACCEPT
2iptables -A INPUT -p udp --dport 138 -j ACCEPT
3iptables -A INPUT -p udp --dport 139 -j ACCEPT
4iptables -A INPUT -p tcp --dport 137 -j ACCEPT
5iptables -A INPUT -p tcp --dport 138 -j ACCEPT
6iptables -A INPUT -p tcp --dport 139 -j ACCEPT
What it does: Allows SMB (Windows sharing) connections to local computer
1iptables -A INPUT -p tcp -s 192.168.1.2 --dport 3306 -j ACCEPT
What it does: Allows MySQL remote connections from IP address 192.168.1.2
See you soon!
